RootMe: TryHackMe: writeup:-

Hi,
This blog is about RootMe room on TryHackMe.Com. This room is free for everyone so everyone can join it. its a simple easy and beginners level CTF.
Description: A guide to complete RootMe CTF.
TASK1: Deploy the machine-
Task1.1:first start the machine and grab the IP Address.Shown in fig 2.0.

TASK2: Reconnaissance-
Now scan the IP Address with nmap. Show in fig 3.0.

Task2.1: Scan the machine, how many ports are open?
2
Task2.2: What version of Apache is running?
2.4.29
Task2.3: Find directories on the web server using the GoBuster tool.
No answer need
— Use gobuster tool for finding hidden directories. Shown in fig 4.0.
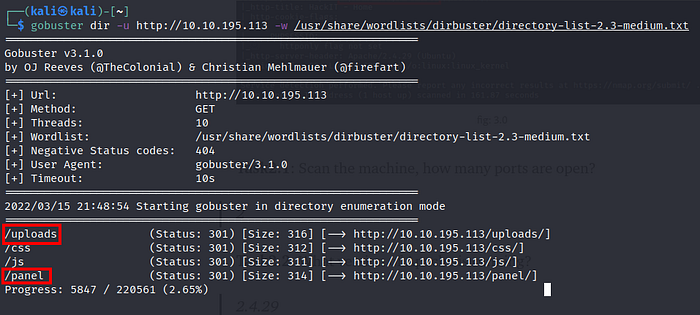
Task2.4: What is the hidden directory?
/panel/
TASK 3: Getting a shell-
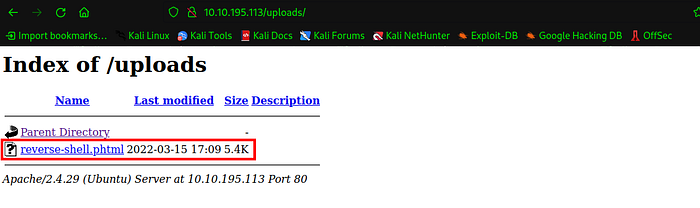
Now lets look whats run on the web. Its seem a normal web page shown in fig 5.0. Now look /panel/ directory and here we get a file uploading page.Its seems we can upload a php-reverse-shell on the server for get a shell. So lets try.First lets download a php-reverse-shell from pentestmonkey.

Now lets configure our reverse-shell.We have to change its IP Address to our tun0’s IP (shown in fig 7.0)and we select port no 1234 you can change it what ever you want.

Now lets try to upload the .php file to serve but we are not permitted to upload Shown in fig 8.0.

Now lets try to change extension .php to .phtml now lets try again, now we are able to upload the reverse-shell successfully.Shown in fig 9.0.

Now start a netcat session for listen on the same port no of which you use in reverse-shell by following command:
nc -lvnp 1234

Now go to following link http://machine_IP/uploads/ and hit to your revese-shell file.You will get a shell.Shown in fig-11.0
Now we get a revese-shell oun our machine. shown in fig 12.0.

Now type the following command to find user.txt.show in fig 13.0:
find / -type f -name “user.txt” 2>/dev/null

Now you can find user.txt in /var/www/user.txt
Task 3.1: user.txt
THM{y0u_g0t_a_sh3ll}
TASK 4: Privilege escalation-
Now we need root.txt, for that we have to escalate our privileges to root user so lets find some thing that should vulnerable. Lets run the command:
find / -user root -perm /4000
We find some files which have permission of 4000 but one file looks weird.Shown in fig 14.0.

Task4.1: Search for files with SUID permission, which file is weird?
/usr/bin/python
Task 4.2: Find a form to escalate your privileges.
no answer needed
Lets find about vulnerability of that python file on GTFOBins .
Now run the following command to read root.txt file:
python -c ‘print(open(“/root/root.txt”).read())’
Now we got the root.txt.shown in fig 15.0.

Task 4.3: root.txt
THM{pr1v1l3g3_3sc4l4t10n}
WOW! we solve the RootMe CTF.Thanks for be here and read the article.
See you in another Article………
